

Attacks on corporate systems can occur not only through direct hacking but also via partners, integrators, or clients who have access to IT infrastructure, corporate systems, CRMs, billing platforms, or databases.
A VPN provides a secure connection over public networks by encrypting traffic to ensure confidentiality. However, a VPN is only one component of an overall cybersecurity strategy.
VPN: Important, But Not Sufficient
To achieve a reliable level of protection, a VPN must be used in conjunction with other security tools, such as:
- Multi-Factor Authentication (MFA) – Verifies user identity on multiple levels. If certain devices (e.g., outdated smartphones) do not support modern MFA apps, authentication via SMS or callback can be used.
- Web Application Firewall (WAF) – Filters application-level traffic, allowing malicious requests to be blocked before they reach the servers.
- Privileged Access Management (PAM) – Monitors the activities of administrators and technical personnel who have elevated access rights.
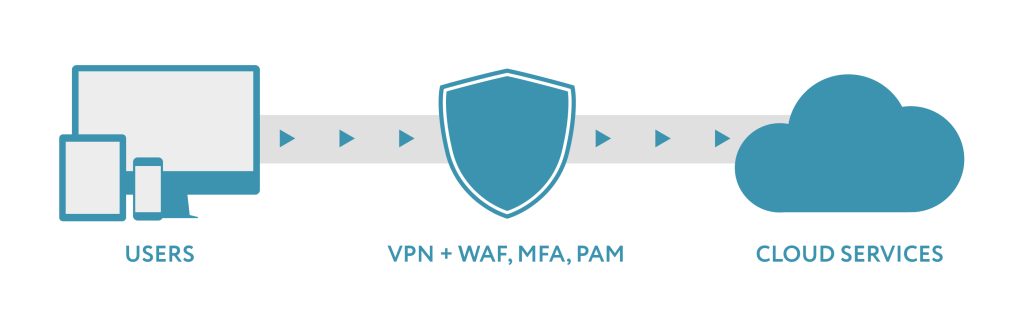
The combination of these technologies creates a system that minimizes the risks of both external and internal threats.
Why Use a VPN in the Cloud?
A VPN creates a secure connection between users and cloud services. It helps control access, encrypt traffic, and protect data from interception—even when users connect from different locations or through public internet networks. VPNs help maintain security and privacy when working with cloud infrastructure.
What You Need to Know:
- VPN encrypts the communication channel but does not protect against account compromise.
- Access must be limited and strictly controlled. Secure backups are essential.
- VPN configurations must be regularly updated and maintained.
Backup Protection as a Guarantee of Data Availability
A VPN is a basic security tool that provides protected access to corporate systems. However, human-related risks – such as accidental errors or intentional deletion – remain a concern. That’s why we implemented Retention Lock Backup, which prevents deletion or alteration of backups. It ensures the integrity of critical data during cyberattacks or incidents caused by human error.
PAM as a VPN Alternative
For companies that prefer not to use VPNs, Privileged Access Management (PAM) offers a robust alternative. PAM enables full control over access privileges and minimizes the risk of errors or malicious actions by users with elevated rights. The system provides detailed user activity audits and automatic password management, and ensures access only to the necessary resources. This significantly reduces the risk of internal threats and account compromise.
However, implementing PAM requires deep technical expertise, additional budget, and considerable team resources. Therefore, this solution is most suitable for IT integrators, data centers, cloud providers, and companies with large administrative teams and complex IT infrastructures.
In combination with MFA, WAF, PAM, and reliable backups, VPN helps provide additional protection for corporate IT infrastructure.



